-88-
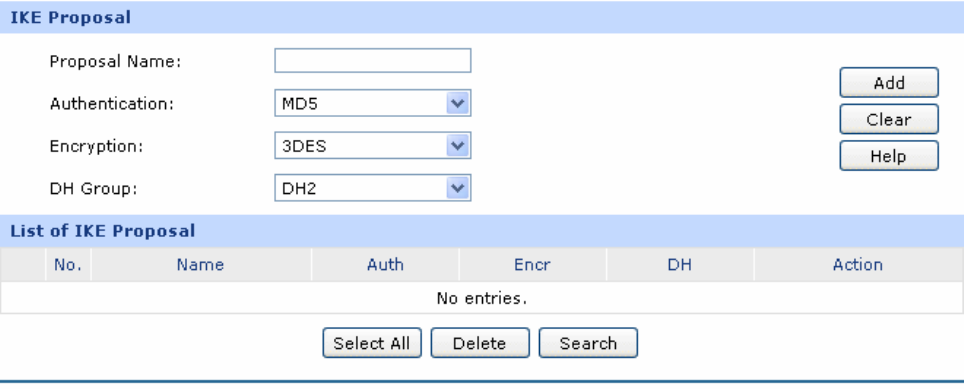
Figure 3-58 IKE Proposal
The following items are displayed on this screen:
¾ IKE Proposal
Proposal Name:
Specify a unique name to the IKE proposal for identification
and management purposes. The IKE proposal can be
applied to IPsec proposal.
Authentication:
Select the authentication algorithm for IKE negotiation.
Options include:
z MD5: MD5 (Message Digest Algorithm) takes a
message of arbitrary length and generates a 128-bit
message digest.
z SHA1: SHA1 (Secure Hash Algorithm) takes a
message less than 2^64 (the 64th power of 2) in bits
and generates a 160-bit message digest.
Encryption:
Specify the encryption algorithm for IKE negotiation.
Options include:
z DES: DES (Data Encryption Standard) encrypts a
64-bit block of plain text with a 56-bit key.
z 3DES: Triple DES, encrypts a plain text with 168-bit
key.
z AES128: Uses the AES algorithm and 128-bit key for
encryption.
